
With 1Password Business, you can integrate 1Password with OneLogin to automate many common administrative tasks:
Provision
- Create users: Provisioned users will be created in 1Password.
To sync groups from your directory to 1Password, use OneLogin roles.
- Update user attributes: Changing user attributes in your directory will change the mapped attributes in 1Password.
- Deactivate users: Deactivating a user or disabling the user’s access to 1Password in OneLogin will suspend the user in 1Password.
Import
- Import users and groups: Existing 1Password users and groups can be imported and linked to existing OneLogin objects.
Manage groups
- Use roles: OneLogin roles can synced to 1Password groups. Role changes in OneLogin will be synced to 1Password.
To get started, sign in to your account on OneLogin.com , select Administration in the top right, and follow these steps.
Before you begin
Before you can integrate 1Password with OneLogin, you’ll need to:
- Set up and deploy 1Password SCIM Bridge.
- Make sure Provisioning users & groups is turned on in the Automated User Provisioning page of your 1Password account.
Step 1: Add the 1Password Business application to OneLogin
These steps were recorded in June 2025 and may have changed since. Refer to the OneLogin documentation for the most up-to-date steps.
To add the 1Password Business application to OneLogin:
- Select Applications, then select Add App.
- Search for 1Password Business and select it. You’ll see the Portal settings for the integration, including the default application label 1Password Business.
- Select Save.
You’ll see the settings for the application you just created.
Step 2: Configure the application
On the 1Password Business application settings page, select Configuration. Then follow these steps.
2.1: Set up API connection
Enter your Base URL and API Token.
SCIM Base URL: the URL of your SCIM bridge (not your 1Password account sign-in address). Use
httpsand don’t include a forward slash (/) at the end. For example:https://scim.example.comIf you don’t know your URL, make sure you’ve set up and deployed the SCIM bridge.
SCIM Bearer Token: the bearer token for your 1SCIM BridgeLearn what to do if you don’t have your bearer token.
Select Enable > Save.
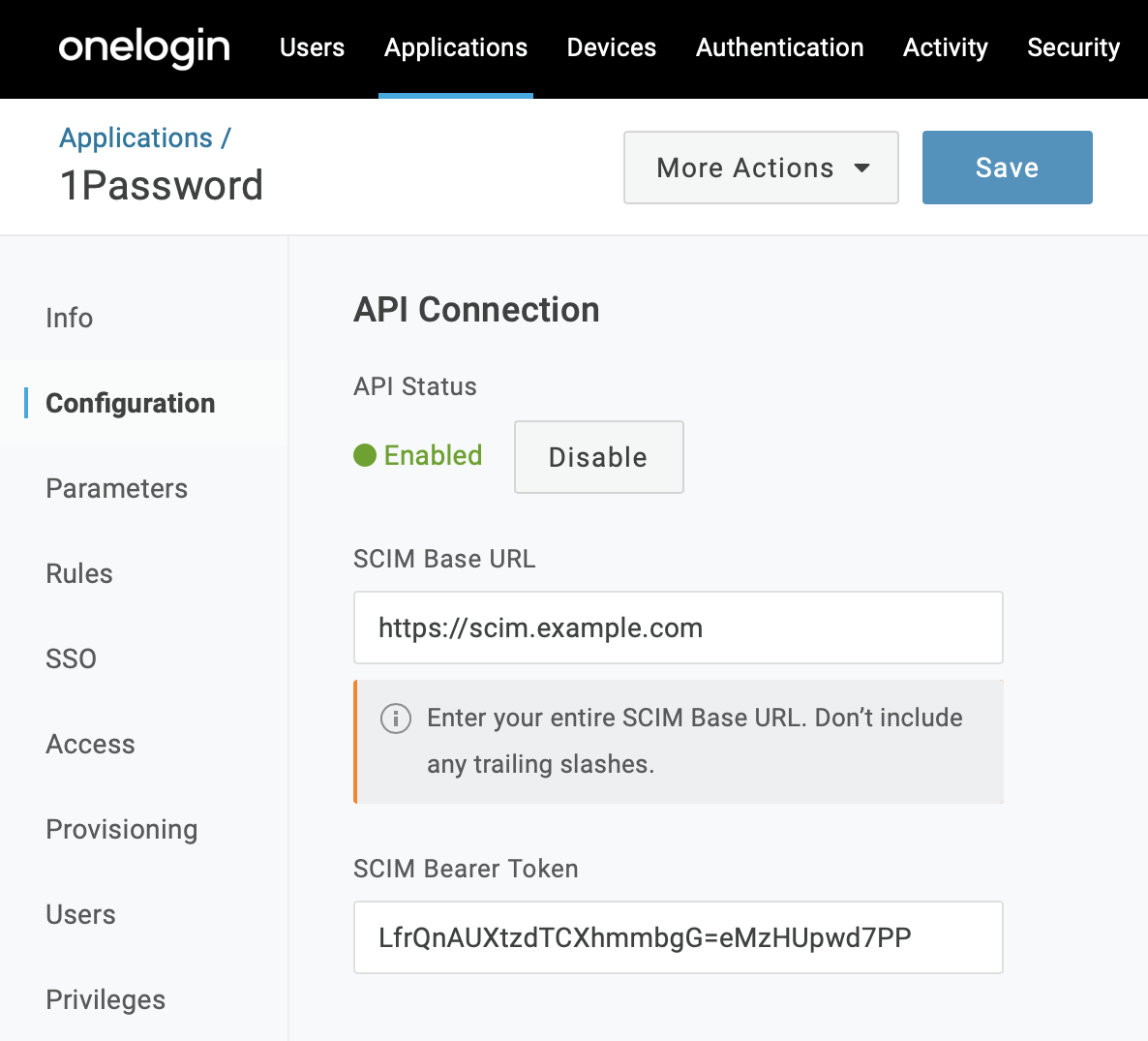
Important
Confirm that your base URL uses https and does not include a forward slash (/) at the end. For example: https://scim.example.com
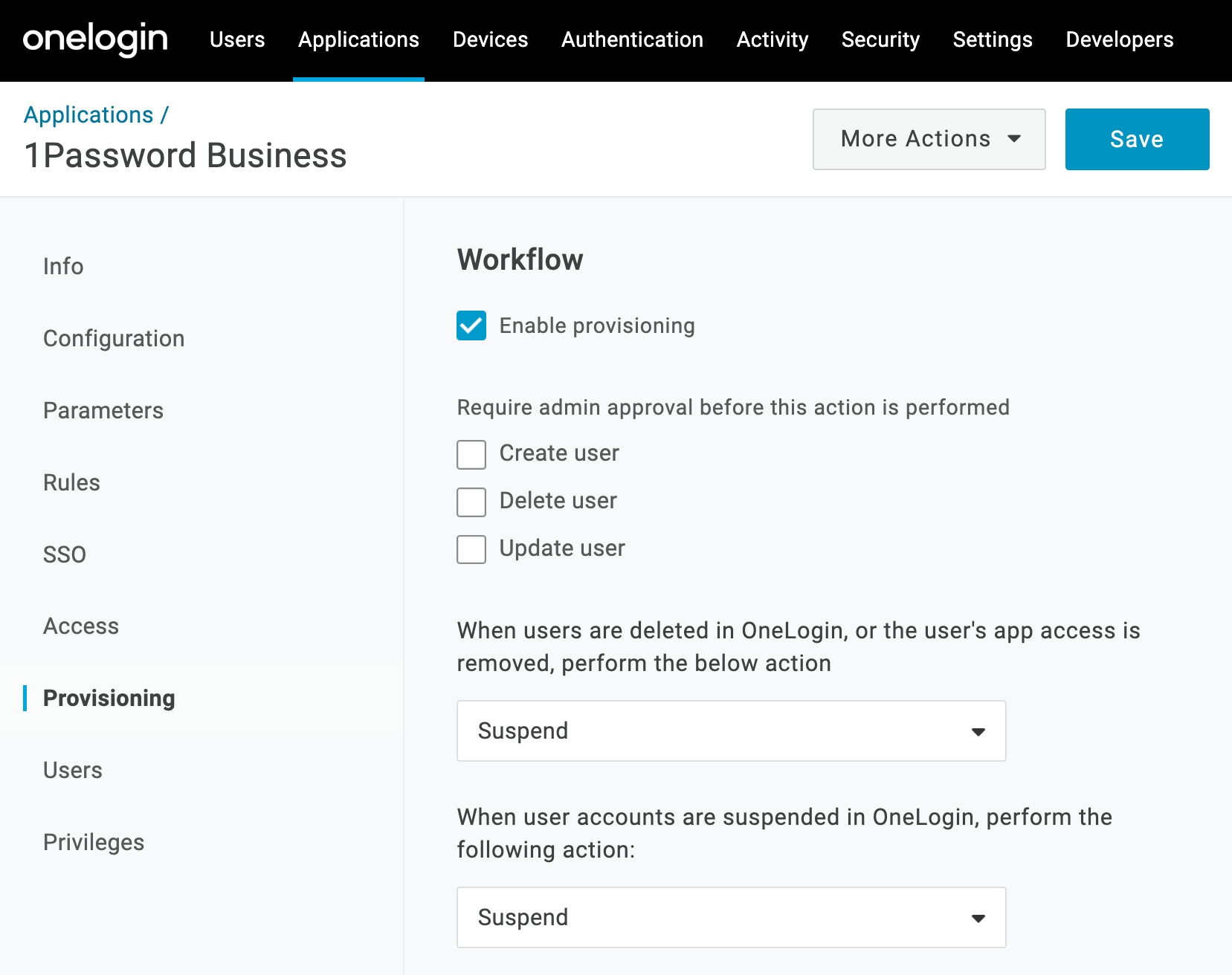
2.2: Set up provisioning to 1Password
- Select Provisioning in the sidebar.
- Turn on Enable provisioning and review the other settings.
- Choose Suspend or Delete under “When users are deleted in OneLogin, or the user’s app access is removed, perform the below action”.
- Choose Suspend under “When user accounts are suspended in OneLogin, perform the following action”.
- If you want to customize the attribute mappings, refer to the default mappings below.
- Select Save.
Next steps
When you turn on provisioning, existing 1Password users will be linked to OneLogin users if their email address matches. If their email address is different, they’ll be invited to 1Password again, so make sure any affected team members update their email address before you turn on provisioning.
If a team member hasn’t accepted their invite after 2 days, they’ll receive a reminder email.
Manage your settings
OneLogin roles can be mapped to 1Password groups. Select Rules in the sidebar to start mapping roles. Learn more about how you can create mappings to automatically assign roles to new users.
To get help pushing roles and their memberships to 1Password when assigned, contact OneLogin Support.
Get help
If users and groups aren’t being provisioned, make sure provisioning is turned on in your 1Password account:
- Sign in to your account on 1Password.com.
- Choose Integrations in the sidebar.
- Choose Automated User Provisioning.
- Make sure Provisioning users & groups is turned on.
Appendix: Attribute mappings
The following are the default user attribute mappings for the 1Password Business application in OneLogin:
| 1Password attribute | OneLogin attribute | Description |
|---|---|---|
| The team member’s username and email address. | ||
| Display Name | Macro
: {firstname} {lastname} | Their full name. |
| First Name | First Name | Their first name. |
| Last Name | Last Name | Their last name. |
Learn how to create a mapping in OneLogin.
Was this article helpful?
Glad to hear it! If you have anything you'd like to add, feel free to contact us.
Sorry to hear that. Please contact us if you'd like to provide more details.