Tip
If you don’t use Google Cloud Platform, you can still automate provisioning in another deployment environment.
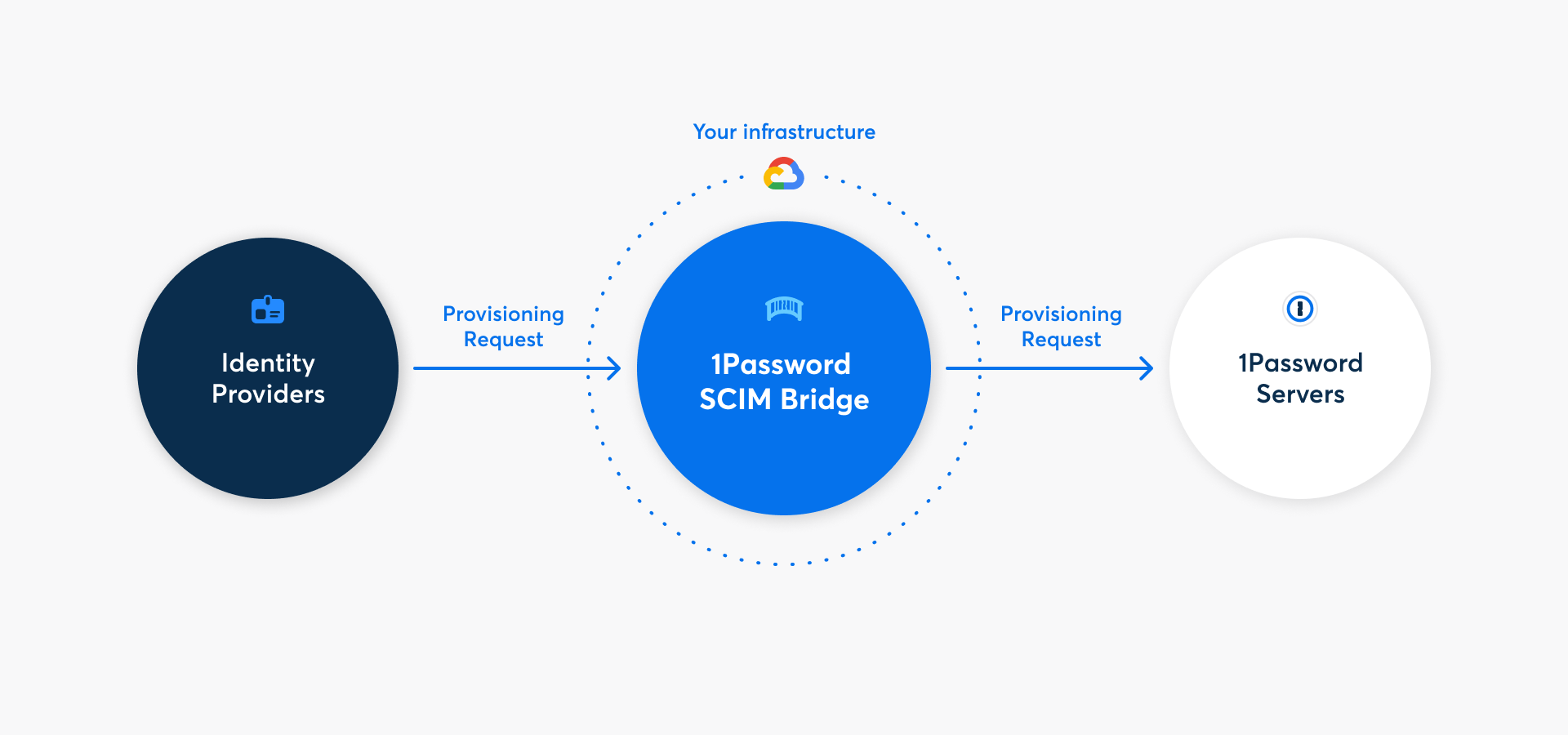
With 1Password Business, you can automate many common administrative tasks using 1Password SCIM bridge. It uses the System for Cross-domain Identity Management (SCIM) protocol to connect 1Password with your existing identity provider, like Google Workspace, JumpCloud, Microsoft Entra ID, Okta, OneLogin, or Rippling.
Step 1: Deploy 1Password SCIM Bridge on Google Cloud Platform
If you don’t already have a Google Cloud Platform account, create one. Then follow these steps.
1.1: Create a project
The SCIM bridge must be deployed within a project. To create a project:
- Visit the Manage resources page and select Create project.
- Enter a project name. If you’re part of an organization, choose it.
If you can’t choose your organization, contact your Google Cloud Platform organization administrator.
- Click Create.
After the project has been created, you can configure the SCIM bridge.
1.2: Configure 1Password SCIM Bridge
Visit 1Password SCIM Bridge on Google Cloud Platform Marketplace and select Configure. If prompted, choose the project you created above.
Tip
If you see “‘Kubernetes Engine Admin’ role is required”, ignore it. The message will go away after you create a cluster.
Fill out the following fields:
- Cluster: Choose an existing cluster or select Create a new cluster. If you create a new cluster, refresh the page after it has been created.
- Namespace: Use the provided default. Or if you have an existing application in the cluster, create a new namespace called “1password”.
- App instance name: Use the provided default.
- 1Password sign-in address: Your 1Password sign-in address. For example:
example.1password.com
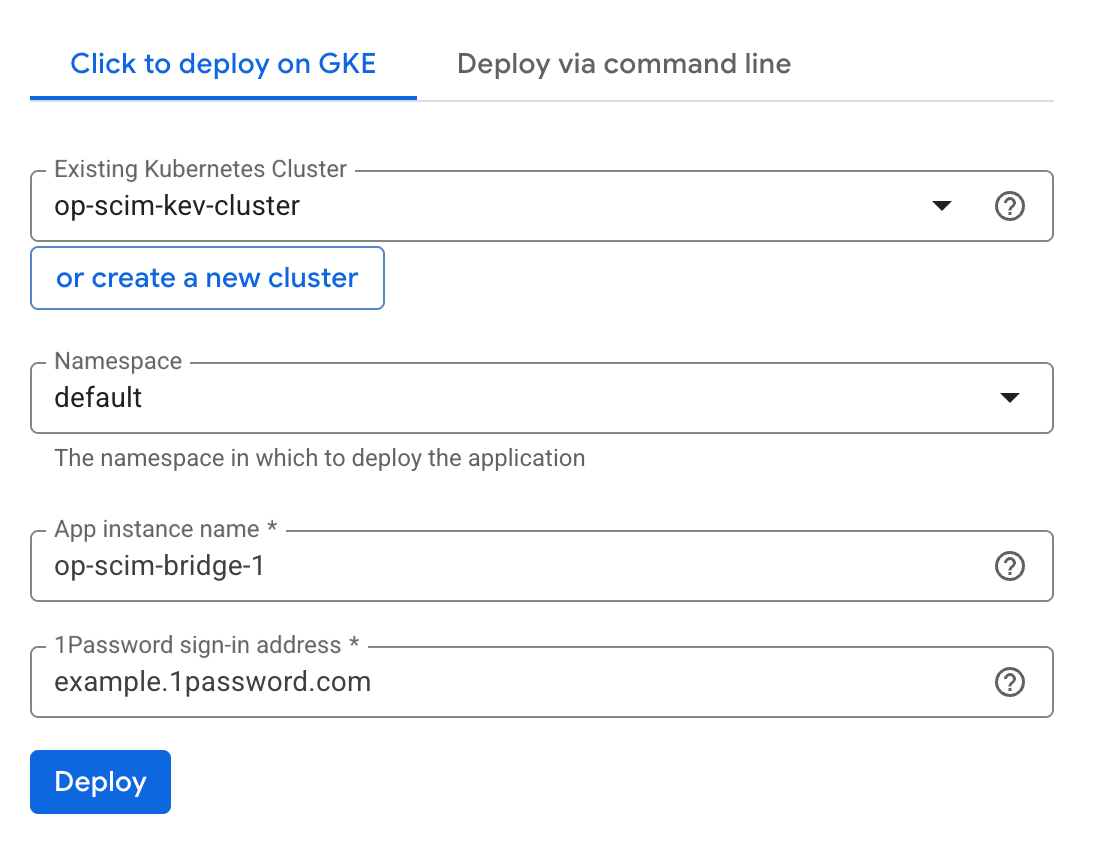
When you’re done, select Deploy. After the SCIM bridge is deployed, you’ll see its application details.
1.3: Set up 1Password SCIM Bridge
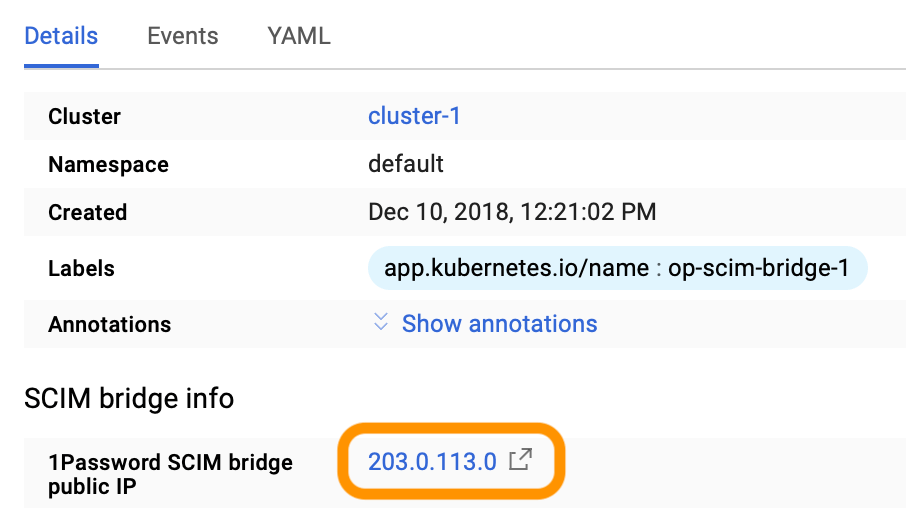
In the “SCIM bridge info” section of the application details, the “1Password SCIM Bridge public IP” begins with 10 (for example, 10.11.255.255), which is a private IP address.
Refresh the page until the IP address changes to a public IP, one that doesn’t begin with 10.
Before you can connect the SCIM bridge to your 1Password account, you’ll also need to:
- Configure a DNS A record for your chosen domain and point it to the IP address of your load balancer. For example:
scim.example.com. - Wait for the DNS to propagate.
Then navigate to your SCIM bridge domain.
Step 2: Connect the SCIM bridge to your 1Password account
2.1: Sign in to your 1Password account
On the 1Password SCIM Bridge setup page:
- Enter the domain name you configured for the SCIM bridge to verify it.
- Click Sign In and follow the onscreen instructions.
Learn what to do if you see the details for an existing provisioning integration.
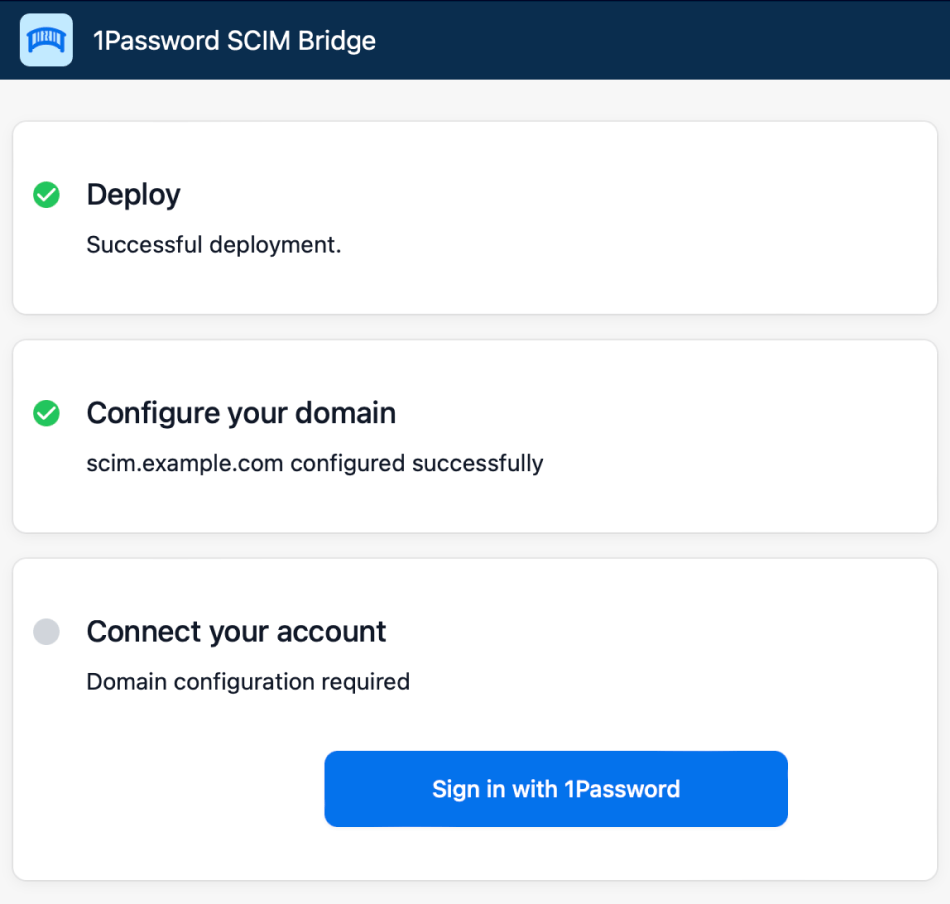
2.2: Authenticate with the SCIM bridge
After you complete the setup process, you’ll get a scimsession file and bearer token. Save them both in 1Password in case you need them again.
- Click Install on <yourdomain>. You’ll see the 1Password SCIM Bridge Status page.
- Enter your OAuth bearer token and select Verify.
Important
The bearer token and scimsession file you receive during setup can be used together to access information from your 1Password account. You’ll need to share the bearer token with your identity provider, but it’s important to never share it with anyone else. And never share your scimsession file with anyone at all.
2.3: Configure a static IP address
When you first deploy 1Password SCIM Bridge, an ephemeral IP address is assigned to it. This address is not guaranteed to remain constant, which may interrupt your automated provisioning.
To use the SCIM bridge without interruption, promote the 1Password SCIM Bridge public IP to a static IP address. Learn how to configure a static IP address.
Step 3: Connect your identity provider to 1Password SCIM Bridge
Important
If you’ve already been using 1Password Business, make sure the email addresses and group names in your 1Password account are identical to those in your identity provider.
- If anyone is using a different email address in 1Password, ask them to change it.
- If you have existing groups in 1Password that you want to sync with groups in your identity provider, adjust the group names in 1Password.
Because 1Password SCIM Bridge provides a SCIM 2.0-compatible web service that accepts OAuth bearer tokens for authorization, you can use it with a variety of identity providers.
Connect to the TLS-secured API gateway, proxy, or load balancer where you’ve configured the SCIM bridge (for example: https://scim.example.com) and authenticate using your OAuth bearer token.
User Guide
Learn how to connect your identity provider:
Get help
Get help with the SCIM bridge, like if you lose your bearer token or session file.
If you have an existing provisioning integration
If you see the details for an existing provisioning integration on the setup page, select Regenerate Credentials, then follow the steps to save the new credentials to your 1Password account and install them on your SCIM bridge. Existing settings for the integration, such as managed groups you selected, will be retained.
If you don’t need to retain existing settings, select More Actions > Deactivate Provisioning. Then select Sign In on the setup page again.
To get more help or share feedback, contact 1Password Business Support or join the discussion with the 1Password Support Community.
Learn more
Was this article helpful?
Glad to hear it! If you have anything you'd like to add, feel free to contact us.
Sorry to hear that. Please contact us if you'd like to provide more details.