About the issue
An issue was discovered in 1Password Secrets Automation. The issue affects anyone using 1Password Connect server 1.1.1 or earlier.
The Connect server doesn’t properly validate input when consuming Secrets Automation tokens, which would permit bypassing authorization restrictions the creator of that token has. As a result, a person with permission to create Secrets Automation tokens can create tokens with access to any vaults configured to be accessed by the Secrets Automation it was created in.
This issue was discovered internally in May 2021, and various mitigations to address the issue were released over the course of May and June 2021. It has been assigned identifier CVE-2021-36758 in the Common Vulnerabilities and Exposures database.
Who may be affected
Anyone who uses 1Password Connect server 1.1.1 or earlier may be affected. You are affected by this issue specifically if:
- You restrict the vault access of the access tokens used in your secrets automations, and
- You created these restricted tokens in the 1Password web app prior to June 7, 2021, or using the 1Password command-line tool 1.10.2 or earlier.
Starting June 28, 2021, all affected tokens will be marked “unverified”. When you sign in to your account on 1Password.com, you’ll see “Action required” next to unverified tokens.
Recommended action
To address risks from unverified tokens, 1Password Connect server 1.2 contains mitigations to prevent most attack scenarios. Furthermore, 1Password will stop accepting unverified tokens on August 2, 2021. Automations that rely on unverified tokens will stop working on that date.
To prevent any interruption in service, upgrade your Connect server deployments and verify your tokens. You can follow these steps if:
- you’re an owner or administrator
- you belong to a group that can manage Secrets Automation
Step 1: Upgrade your Connect server deployments
Everyone using 1Password Connect server should upgrade to version 1.2 or later.
- Docker: Edit your
docker-compose.yamlfile to use the latest available versions of theconnect-apiimage andconnect-syncimage. - Kubernetes: Perform a
helm upgradeon your Connect server deployment to upgrade to the latest available version.
If you don’t have any current Connect server deployments, you can skip this step. To prevent issues if you plan on using your existing tokens in future deployments, continue to the next step.
Step 2: Verify your tokens
If you have automations that rely on specific tokens, you can verify them, so they can continue working. Only verify tokens that you have confirmed have the access you expect. To verify a token:
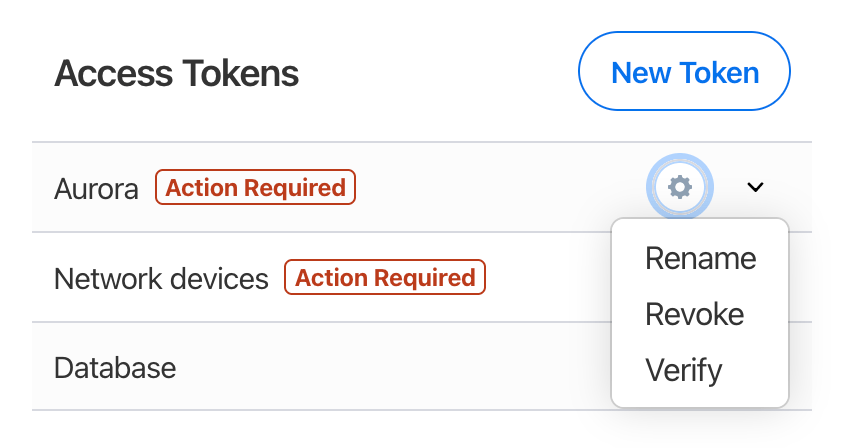
- Sign in to your account on 1Password.com and click Integrations in the sidebar.
- Choose the Secrets Automation environment you want to verify a token in.
To verify a token’s access, click the down arrow . Make sure the vaults the token has access to are the ones you expect.
- Click the gear button next to the token you want to verify, choose Verify, and enter the token.
If you have unverified tokens that you no longer need, click the gear button next to the token you want to revoke and choose Revoke. After you revoke a token, you can generate a new one.
If you use the 1Password command-line tool
If you use the 1Password command-line tool to manage your Secrets Automation tokens, upgrade to 1Password command-line tool 1.10.3 or later to make sure you are generating tokens that continue to be compatible with Connect server 1.2 and later versions.
To check your version, run op --version.
To audit token usage history
Your 1Password Connect server keeps event logs for tokens that attempted to access vaults they shouldn’t have access to. To verify whether any tokens have been used outside of their created authorizations, audit this history.
To facilitate your audit, you can use the access token audit tool, a script that compares your Connect server’s event log with the tokens registered in your 1Password account. To use the tool, make sure you’ve set up the 1Password command-line tool and have Python 3 installed. Then download the access token audit tool and follow the instructions in the script’s comments.
Impact and exploitability
The 1Password Connect server is a tool for IT administrators use in their own networks to automate using secrets stored in 1Password in deploying and maintaining infrastructure. This bug doesn’t affect anyone that doesn’t use 1Password Secrets Automation.
This issue allows users that have restricted access to create tokens to bypass those restrictions. For example, suppose you have a 1Password account with 10 vaults, and a Secrets Automation is configured to provide access to 3 of them: Foo, Bar, and Baz. If Alice can create tokens that can access only the Foo vault, this issue allows Alice to create a token that allows access to Foo, Bar, and Baz - all 3 vaults the Secrets Automation may access. In addition, Alice is also able to set other arbitrary attributes on the token, such as arbitrary expiry dates. To do this, Alice must manually create these tokens in a way that’s not offered by the 1Password web app or command-line tool.
Permission to create tokens in many circumstances already constitutes a certain level of privileged access for that user - usually limited to a set of IT administrators. Nonetheless, within this group many will want to enforce a principle of least privilege when creating tokens. This issue can be used to circumvent enforcement of that principle.
This issue does not allow extending access to vaults beyond what the Secrets Automation was configured to access. In the example above, it did not allow Alice to create tokens to access the remaining 7 vaults that were inaccessible to the Secrets Automation.
Commentary
A wise person once said - “given enough eyeballs, all bugs are shallow”. Given the amount of eyes we’ve had on this, we should have found this issue prior to release. Missing validation leading to an authorization problem is a terrible class of bugs, and we apologize for releasing a product with one.
We’ll update our development process to reduce the chance that bugs of this class will slip through in the future. We’re investigating means of authentication and authorization that are less susceptible to the class of bugs discovered here.